BYOD might be the corporate buzz word for 2012. If you’re in the dark, BYOD stands for Bring Your Own Device. It represents employees connecting their own mobile devices to corporate networks, instead of using employer-issued devices. There was a time, not all that long ago, when Blackberry was the mobile device of corporate America. Once iOS and Android started supporting email via Exchange, however, executives started questioning why they needed to carry a work device and a personal device. In short, they wanted their email and Angry Birds wrapped up in one tidy mobile package. Thus, the birth of BYOD. Today, Blackberry is going they way of Betamax, and BYOD is here to stay. I call the iPhone-ification of corporate America.
BYOD, however, is not without its risks. Over at The HR Capitalist, Kris Dunn offers the following sample BYOD Policy (c/o Scott Stone):
We expect each team member to provide their own device – you select it, you buy it, you pick the plan that makes the most sense for you. Your phone, your phone number, your provider of choice, your contract with the provider
We strongly recommend a “Smartphone” of some type, to ensure you can receive emails or other critical communications on the device.
Our Company will provide you access to your work email address on the device, including assisting you with the setup.
If your device is a “Smartphone”, our company will reimburse you $75 per month to cover all work related communications on the device (email, text, voice, communications, etc). We expect you to select a plan which can accommodate your business and personal needs for voice and data
If you select a PO Phone (plain ‘ol phone) which lacks the ability to receive and send emails, our company will reimburse you $15 per month for all work related communications
We won’t provide a “company phone” to anyone, preferring to allow you to “BYOD”, and provide everyone maximum flexibility.
If you ever choose to leave the company, take your phone, your number, and your existing agreement with a provider – no hassle, no number change, no problem.
These seven points have one glaring omission—security. The biggest risk that BYOD creates is the seemingly uncontrolled access to your network, both in terms of what information is accessed and take from it, and what happens to that information if a device is lost or stolen. In light of these security risks, any BYOD program should answer the following 5 questions:
-
What devices are permitted? Does BYOD mean any device, or does it simply mean iPhones or Androids? What about iPads or other tablets? Employee-owned laptops? Stick drives and other portable memory?
-
Are you going to mandate passwords or other security-screens on network-connected devices? Employees generally resist having to enter a four-digit pin code every time they turn on their iPhones. Your IT, legal, and risk management departments, however, should require them, since they make it that much harder for someone to access data on a lost or stolen device. If your organization deals in confidential information (e.g., doctors, lawyers, etc.), this requirement is that much more important (and might be mandated by law). Also, your BYOD policy should reference any other policies that address the handling of confidential and proprietary information.
-
What happens when a device is lost or stolen? IT must have the ability to remote-wipe a missing mobile device. Guess what happens, though, if an employee’s first call upon losing a phone is to their mobile carrier? The carrier turns off the device, and your organization loses the ability to remote wipe any data from it. Employees should be told that if they lose a mobile device, their first call should be to IT so that the device can be wiped of any corporate data.
-
Will you ban jailbreaks, roots, and other hacks? These practices void the phone’s warranty. Also, consider banning the installation of apps other than from the official iTunes App Store or Google Play. It will limit the risk of the installation of viruses, malware, and other malicious code on the devices.
-
What happens when an employee leaves? You should not only address what happens with the physical device, but also what happens with the data that lives on the device. You need a protocol to re-acquire or wipe all corporate information on the device. Otherwise, you are putting your confidentiality at risk.
Any successful BYOD program results from a synergy among the C-suite, legal, IT, HR, and risk management. Involve all of these departments to make sure that your BYOD program is successful, and addresses all necessary security issues.

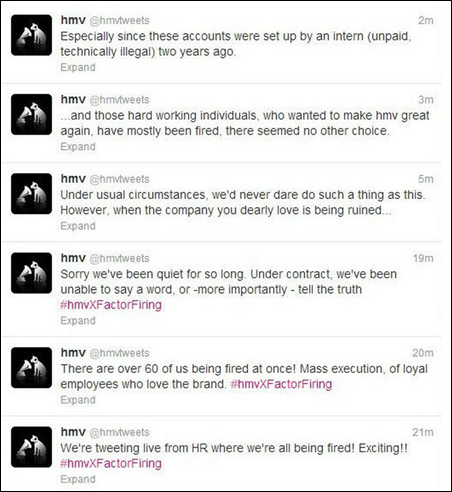

 In
In 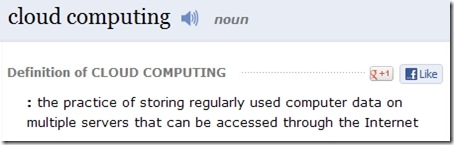
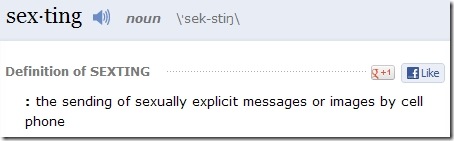
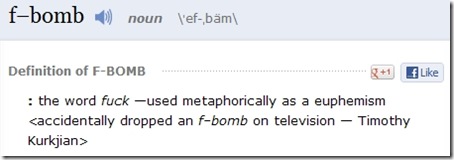




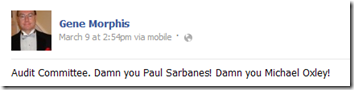
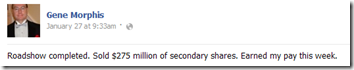
 The public outcry against employers requiring the job applicants turn over their Facebook passwords has resulted in legislation. Maryland has become the first state to prohibit employers from requiring or seeking user names, passwords, or any other means to access Internet sites such as Facebook as a condition of employment. Demonstrating the outrage over this issue, the measure
The public outcry against employers requiring the job applicants turn over their Facebook passwords has resulted in legislation. Maryland has become the first state to prohibit employers from requiring or seeking user names, passwords, or any other means to access Internet sites such as Facebook as a condition of employment. Demonstrating the outrage over this issue, the measure 