Let's see how good your cyber-awareness is.
Do you know the top method of cyber-attack?
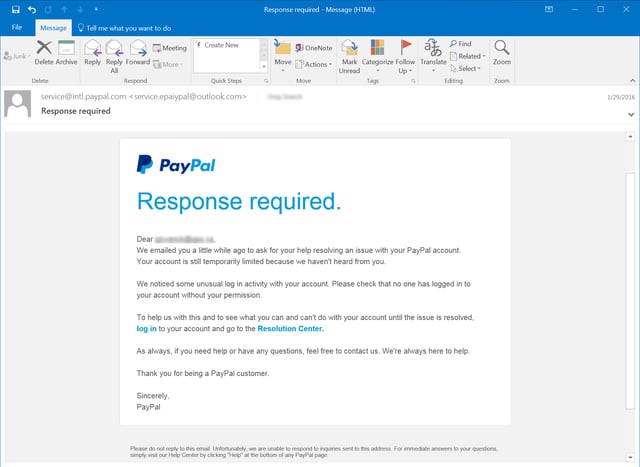
Phishing — the crafting of a message (typically via email, but also via text message or other communication) designed to influence one to "take the bait" via a simple mouse click, sometimes a malicious attachment, but also a link to a webpage that will request logins and passwords or install malware.
According to Phishing.org, there are five key attributes of most phishing attempts:
- Too Good To Be True - Lucrative offers and eye-catching or attention-grabbing statements are designed to attract people’s attention immediately. For instance, many claim that you have won an iPhone, a lottery, or some other lavish prize. Just don't click on any suspicious emails. Remember that if it seems to good to be true, it probably is!
- Sense of Urgency - A favorite tactic among cybercriminals is to ask you to act fast because the super deals are only for a limited time. Some of them will even tell you that you have only a few minutes to respond. When you come across these kinds of emails, it's best to just ignore them. Sometimes, they will tell you that your account will be suspended unless you update your personal details immediately. Most reliable organizations give ample time before they terminate an account and they never ask patrons to update personal details over the Internet. When in doubt, visit the source directly rather than clicking a link in an email.
- Hyperlinks - A link may not be all it appears to be. Hovering over a link shows you the actual URL where you will be directed upon clicking on it. It could be completely different or it could be a popular website with a misspelling, for instance www.bankofarnerica.com - the 'm' is actually an 'r' and an 'n', so look carefully.
- Attachments - If you see an attachment in an email you weren't expecting or that doesn't make sense, don't open it! They often contain payloads like ransomware or other viruses. The only file type that is always safe to click on is a .txt file.
- Unusual Sender - Whether it looks like it's from someone you don't know or someone you do know, if anything seems out of the ordinary, unexpected, out of character or just suspicious in general don't click on it!
As we, as targets, have gotten better at recognizing phishing attempts, the cyber-criminals have gotten better as disguising their phishing to make the emails and other messages seem more legitimate.
Social engineering is the new wave of phishing. Social engineering attacks use information we make publicly available via Facebook, Twitter, LinkedIn, etc., to craft phishing attacks that are more direct and personalized, which increases the likelihood of success.
What is one to do to be as cyber-safe as possible?
The FBI's Internet Crime Complaint Center (IC3) recently reported that cybercriminals are targeting online payroll accounts via sophisticated phishing schemes, and recommends that employers take the following steps to best defend against phishing attacks.
- Alert and educate your workforce, including preventative strategies and appropriate reactive measures should a breach occur.
- Instruct employees to hover their cursor over hyperlinks included in emails they receive to view the actual URL. Ensure the URL is actually related to or associated with the company it purports to be from.
- Instruct employees to refrain from supplying log-in credentials or personally identifying information in response to any email.
- Direct employees to forward suspicious requests for personal information to the information technology or human resources department.
- Ensure that log-in credentials differ from app to app and site to site.
- Monitor employee logins that occur outside normal business hours.
- Restrict access to the Internet on systems handling sensitive information or implement two-factor authentication for access to sensitive systems and information.
- Only allow required processes to run on systems handling sensitive information.
Data breaches are not if issues, but when issues. Even the best monitoring and employee training can only reduce the incidence of successful phishing attempts to two percent. In other words, nothing is foolproof. Indeed, the average cost of a successful phishing attack for a mid-size company is $1.6 million.
If you'd like to know more about how to best protect your business from phishing and other cyber-attacks, including drafting cybersecurity policies and implementing training, I know at least employment lawyer available to help (hint, hint).
For more tools to help your business become more cyber-aware, the Department of Homeland Security has published a helpful toolkit for National Cybersecurity Awareness Month.